IT Researcher Discovers Huge Facebook Exploit, Gets Account Disabled for His Efforts
posted Sunday Aug 18, 2013 by Nicholas DiMeo
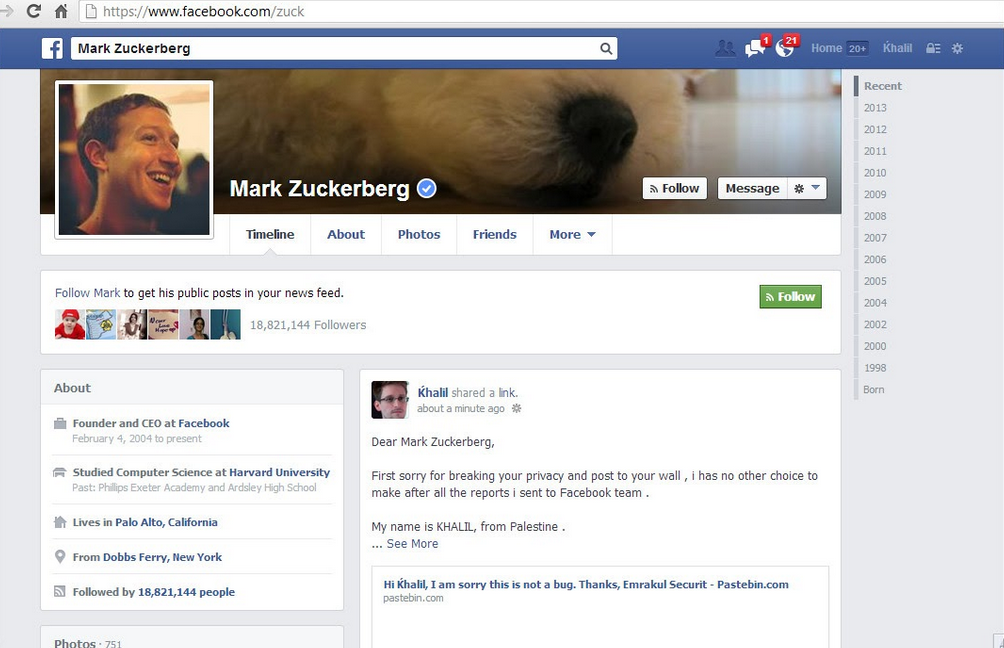
We've talked about vulnerabilities a lot in the past, to the point where we had to recap all of them. Even though we haven't gone into a lot of detail about Facebook's security issues, the social networking giant also has its faults, to the point where they will pay you to find bugs, but only if you report them correctly. This is what Palestinian IT researcher Khalil Shreateh discovered this week, when he identified a major flaw in Facebook's security.
Shreateh wrote to Facebook that there was an ability to post on someone's wall without being friends with them. He then wrote to Facebook, and when the company ignored him by saying "I am sorry this is not a bug," Khalil then took to Zuckerberg's wall to prove his exploit.
He posted a link to his findings, along with his story of what's transpired so far, and, within a handful a minutes, one of Facebook's lead security engineers responded to him, asking him for further information about his discovery. However, what came next is something that shocked some tech journalists, but was something I would not put past Facebook. Because Khalil took to the Zuck's page and posted the exploit there, after numerous email attempts, not only did Facebook temporarily disable his account, they also said they would not be paying him because of improper reporting methods. In an email to the researcher,
We are unfortunately not able to pay you for this vulnerability because your actions violated our Terms of Service. We do hope, however, that you continue to work with us to find vulnerabilities in the site.
While Mr. Shreateh might not have the best English and grammar, his blog post indicates the exact issue he discovered, along with, what he understood based on reading Facebook's procedures, his best attempts at reaching out to the company. It is clear though that he did not precisely outline his discovery in the first email, potentially causing this whole thing to snowball.
In this thread on HackerNews, a Facebook employee chose to provide a bit of clarity on the subject.
We get hundreds of reports every day. Many of our best reports come from people whose English isn't great - though this can be challenging, it's something we work with just fine and we have paid out over $1 million to hundreds of reporters. However, many of the reports we get are nonsense or misguided, and even those (if you enter a password then view-source, you can access the password! When you submit a password, it's sent in the clear over HTTPS!) provide some modicum of reproduction instructions. We should have pushed back asking for more details here.
I get that, but perhaps Facebook should shell out the money anyway, at the very least. I mean, he was bold enough to take the exploit right to the Facebook page of the head of the company. That's pretty brave. You can check out the video of the walkthrough of the exploit after the break.

